DDoS Protector
Lightning fast DDoS Protection with hardware acceleration on commodity NICs.
Optimized for rapid processing
Our DDoS Protector is designed for speed. It’s built on hardware acceleration using DPDK to achieve wire-speed throughput, which we’ve measured at up to 100 Gbps on NVidia ConnectX-6 DX. This means that packet processing is lightning-fast and DDoS attacks stand no chance.

Based on commodity hardware
DDoS Protector is a flexible and efficient solution that works with standard network cards. We measured the best results on Mellanox ConnectX 100G cards and our in-house developed FPGA network cards. Simply install our software and you are ready to go!
Quick and easy configuration
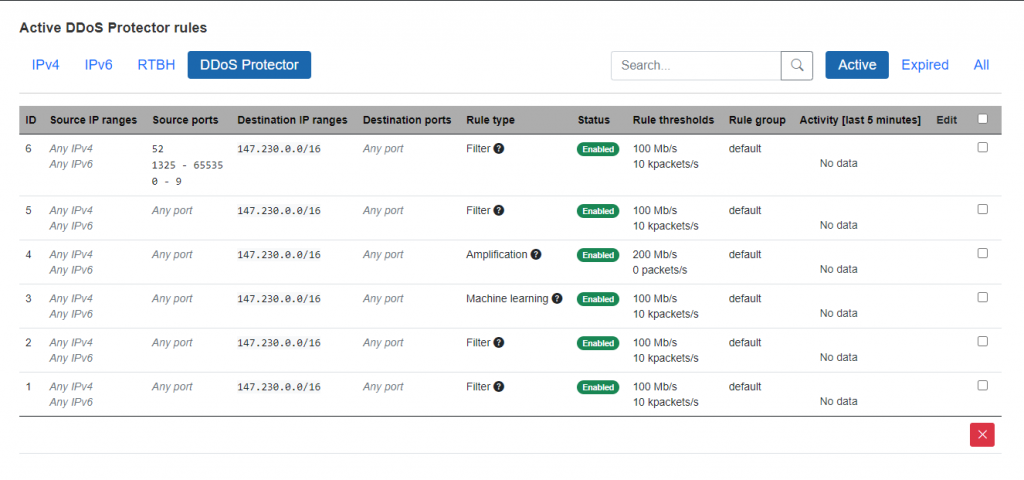
DDoS Protector gives you the flexibility to manage your mitigation settings from anywhere. Whether you prefer a user-friendly web interface or a powerful command line tool, you can easily customize the filtering criteria and choose the best mitigation strategy for your needs. DDoS Protector will take care of the rest and protect your network from malicious traffic.
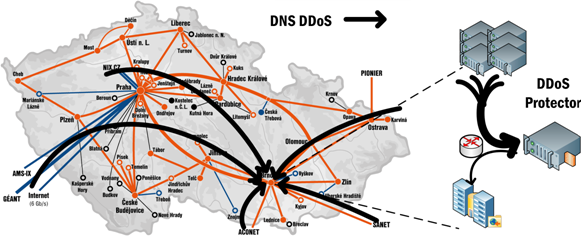
On-premise DDoS Protection
All DDoS protection is done locally in your datacenter. Unlike cloud-based solutions, our solution does not require you to send your traffic to a third party. This means you have full control over your data and you can enjoy faster response times and lower latency.

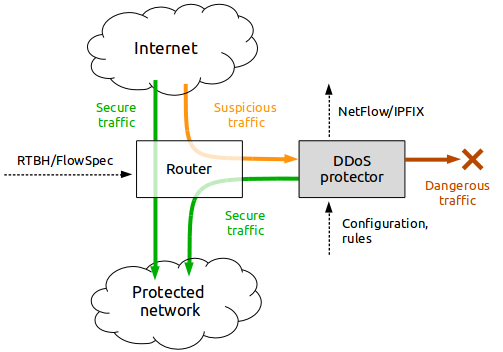
Fits your infrastructure
You don’t have to change your network architecture to enjoy the benefits of DDoS Protector. Whether you want to install it in-line and have it monitor and filter all your traffic, or you want to keep it on standby and redirect traffic to it only when an attack is detected, DDoS Protector can adapt to your needs. It is designed to seamlessly integrate with your existing infrastructure and provide you with the best protection against DDoS attacks.
Multiple modes of mitigation
DDoS Protector provides specialized modes of mitigation to mitigate the attack efficiently while minimizing impact on legitimate traffic.
Simple filtering
Fast and efficient ACL-like traffic filtering.
SYN flood mitigation
Multiple specialized methods for mitigating SYN flood attacks.
Amplification attack mitigation
Block amplification attacks while allowing legitimate traffic.
IP address/prefix filtering
Use reputation databases or IP blacklists to prevent suspicious IPs from attacking.
Adaptive machine learning
Mitigate attacks automatically using machine learning algorithms that analyze the attacking traffic for you.
Capture traffic
Use our hardware accelerated solution to capture samples of traffic for later analysis.
Block by geolocation
Quickly respond to foreign threats by blocking traffic based on their source geolocation.
Customize with plugins
Use our hardware accelerated solution to capture samples of traffic for later analysis.
Contact us!
If you are interested in DDoS Protector for research purposes, you can contact us at ddp@cesnet.cz and request a demo.
Commercial deployment and support is available through our partner HighPPS Networks.